Notes.⚫
This is basically a micro-blog. This is where I post notes, videos, images, back-links and random thoughts.
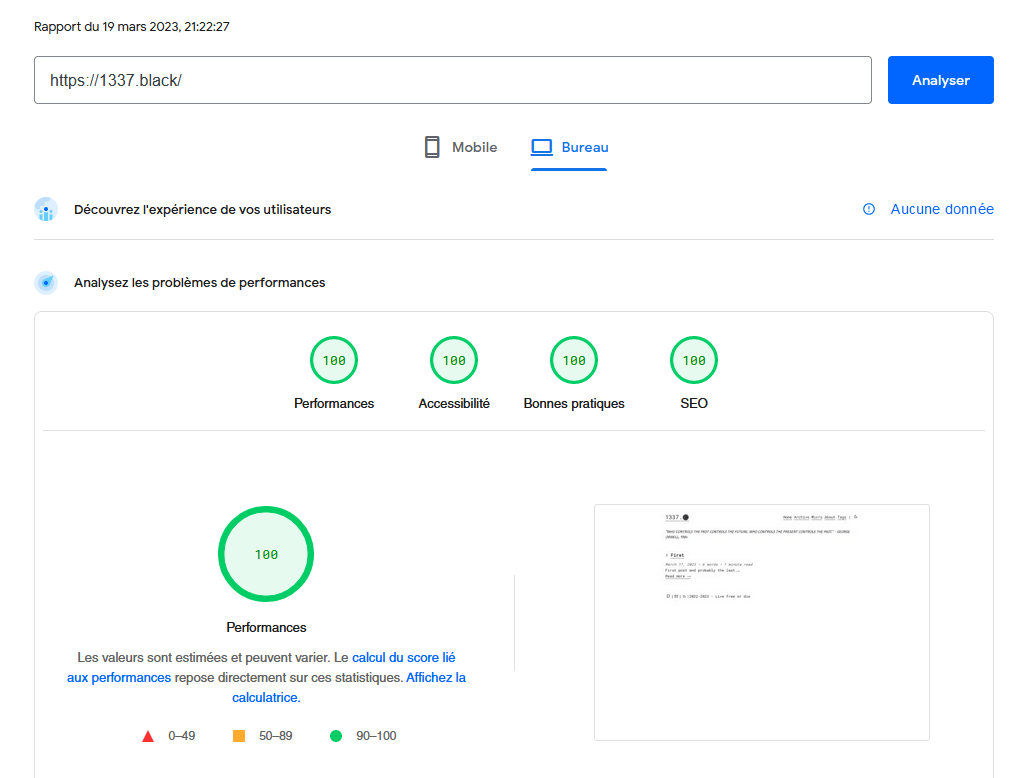
- Load balancing the clearnet site
- Use OnionBalance to load balance my tor requests
- Add an IPFS mirror
- Add back an I2P mirror
- Add a zip archive of the site (I would have to clean the code first)
Permalink ⟶Really interesting movie to see how the EU works and how much lobbying is involved against privacy. It is old but still very relevant considering Chat Control. Thanks to the Pirate Party I guess.
I like to overcomplicate things.
Todo:
PS: you can see on the footer of the clearnet page which pop you are connecting trought.
Permalink ⟶Modern online productivity tools are just like Google tools, the same level of privacy, the same “modern” ui, surfing the ai wave and an objective of retaining user attention and make you loose time.
Permalink ⟶This website now features printer-friendly styling. Not that I think anyone wants or even should print or export any of my articles as a PDF, but the possibility is now here.
This was done to experiment with Priting media queries and because I like and wanted to try to reproduce newspaper like aesthetics.
Permalink ⟶Permalink ⟶TL;DR: we have discovered XMPP (Jabber) instant messaging protocol encrypted TLS connection wiretapping (Man-in-the-Middle attack) of jabber.ru (aka xmpp.ru) service’s servers on Hetzner and Linode hosting providers in Germany.
The attacker has issued several new TLS certificates using Let’s Encrypt service which were used to hijack encrypted STARTTLS connections on port 5222 using transparent MiTM proxy. The attack was discovered due to expiration of one of the MiTM certificates, which haven’t been reissued.
There are no indications of the server breach or spoofing attacks on the network segment, quite the contrary: the traffic redirection has been configured on the hosting provider network.
The wiretapping may have lasted for up to 6 months overall (90 days confirmed). We believe this is lawful interception Hetzner and Linode were forced to setup.