1053 words
March 25, 2023
5 minutes read
How a secure and resilient website should be hosted
Introduction
Hello, following my last article on the opsec of the breached funder pompompurin who lead to his arrest and the fake news about it I wanted to do a new one on how a website may host itself for resiliency and security.
For that I have two pretty simple setups that I can think of with one of them being more easy to implement and probably a lot more stable while not being as secure as the second one.
WAF -> RPROXY 1 -> RPROXY 2 -> VPN -> BACKEND
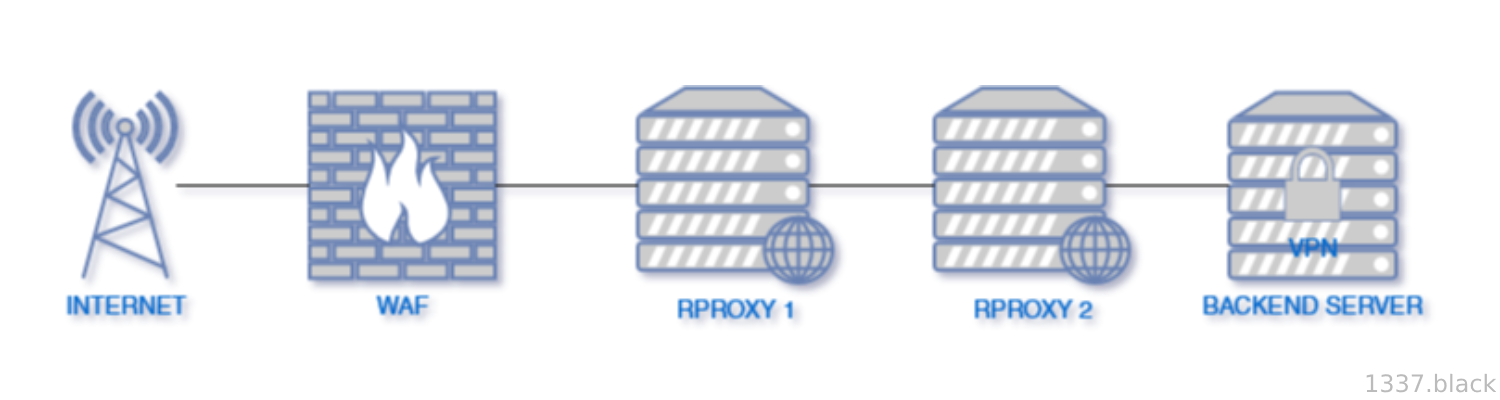
So this first setup is pretty simple. First, for the waf I think the two main possible choices would be cloudflare or ddos-guard. For security and resiliency I would use ddos-guard but cloudflare also have a lot of others features and configurations option while being free which may make it a better choice for a smaller less important forum.
Then, the second and third protections would be reverse proxies, they are useful for multiple reasons. First, if you use cloudflare even if they do not suspend sites following legal orders they do forward all the account records they have linked to your domain. It mean that they would have all of the dns records on your account and so have the ip of your server. It may seems pretty obvious but I have seen a lot of websites thinking an “offshore host” behind cloudflare is sufficient. These reverse proxy would also protect any dmca/abuse forwarded by cloudflare to the website hosting provider (which would be the reverse proxy in this case). These two reverse proxies would have to be on two different hosts known for their respect to privacy and ignorance of most things (like nicevps.net, svea.net, privex.io, buyvm.net, etc).
Then, after the waf and the two reverse proxies as a measure to protect the server in the occasion of the backend ip leaking we would have a reputable vpn on the backend server itself. For that we would need a vpn with port forwarding possibilities (I would use ovpn.net, ivpn.net or mullvad.net). This would shield your server in case the 3 proxies that there is before are somewhat compromised. It would also permits to hide the backend ip in other cases like if your server ip was leaking cause of a vulnerability in your website.
This is also important to know that for this setup to work you would have at any stage of your setup to make web ports only be accessible by the service before it. This would look like RPROXY 1 only allow WAF ips to contact him on port 80 and 443, RPROXY 2 allow only RPROXY 1 ips and your backend server only allow connections from RPROXY 2 ip. If you do not do that your backend ip will end up on indexing websites like censys.io or shodan.io wich is something you do not want to happen.
I never tried to add that to the chain but I’m pretty sure to obscure the traffic coming in and off of your different proxies you could have multiple “fake” servers behind where you would send a copy of the packets you send to the next server on the chain, it would not be that helpful unless you have a lot of servers but I wanted to mention it.
To conclude, this setup is pretty bulletproof but still rest on the normal internet. What I mean by that is that if your adversary is the fbi like for breached they could just subpoena every step of your setup and end up finding your backend. It shouldn’t arrive without you noticing anything if you choose good hosts, countries to host and VPNs but still, this is technically not bulletproof.
WAF -> Clearnet PROXY -> tor
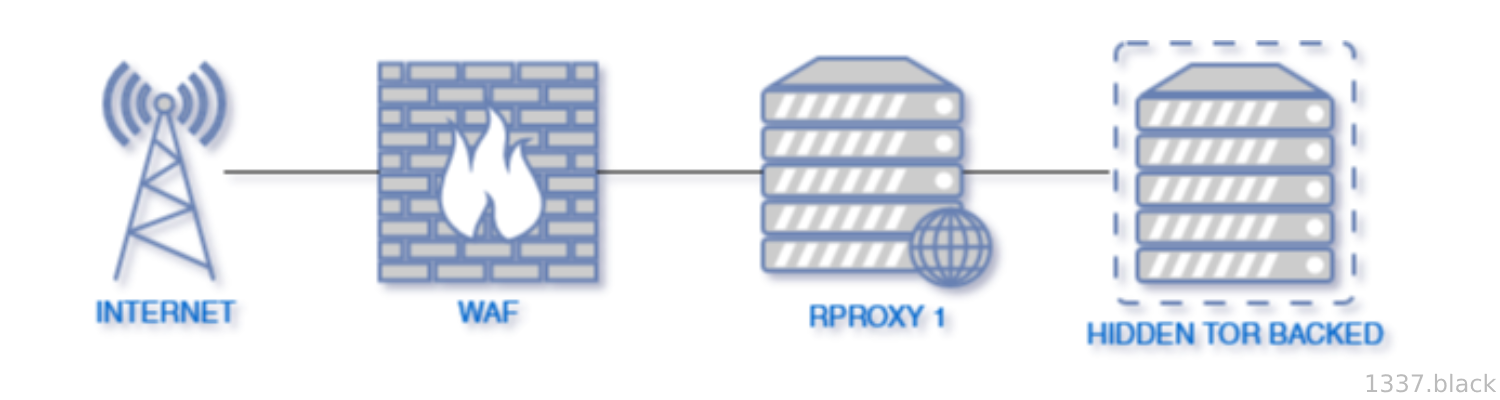
You probably heard of Tor2web proxies haven't you ? These proxies which are most of the time setup to perform mitm attacks are proxies which permit for example to enter something like dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion.sy.st and basically to visit tor domains on the clearnet.
Now, the idea of this setup would be to host your website securely on tor (I will not explain how to do it here as there is already some good articles on that) and to setup your clearnet domain only to proxy the requests to your tor website by installing a Tor2web like proxy on your proxies servers.
I haven’t much experience with this setup but I have still done some tests using this setup in the past and everything worked fine for days without me noticing any issues.
Now, I must also talk about the principal problem that this setup imply. The biggest problem is that it would be pretty instable, websites on tor are already instable but add a proxy before that which tor haven’t been designed for and you get something experimental. Add to that a forum software which have probably been made for far more simples environments and you get something which would probably not work for a forum.
However, I find this setup interesting as even if it is not really useful for a forum where user need to stay logged in and where you do not want connections to time out while doing a post it may be useful for other sites. Pretty much any site which haven’t any user generated content and which doesn’t need a good uptime could benefit from this setup. Imagine for that your small torrent tracker, your private forum, your blog that everyone want down, your leak that you want to share on the Clearnet securely (but it would better not be to big with tor speeds), etc.
Conclusion
To conclude, the first setup would probably be fine if setup and monitored well. If more security is needed nothing prevent you from adding more proxies on different countries to the setup to try to play on local laws. The second setup however, is more what I would consider a proof of concept and at this point you would probably be better of just educating your users on how to use tor and host your website there.
Thanks for reading all of that and I hope you learnt something today, if you have questions or corrections about what I wrote do not hesitate to send me an email to the email address bellow.