1086 words
March 23, 2023
6 minutes read
FUD news in cybersecurity and pompompurin arrest
Introduction
Everyone who has some interests in cybersecurity should know that there is a lot of news sites in the cybersecurity space that are just reposting each others content without any research except on how they could turn the news into the biggest news possible. I will discuss here the two most prevalent fake news about the pompompurim arrest with evidence in an effort on how not to fall into such fake news.
Pompompurin arrest
Pompompurin was the funder of the now defunct forum breached. Pompompurin founded breached right after the arrest of omnipotent, the funder of raidforums. Breached gained in popularity pretty fast spurred by the good reputation of pompompurin on raidforums and how semblable the forum was to raidforums.
From what I saw and from talking to him, I can say that pompompurin was really doing everything he could to satisfy peoples and to make the best out of breached. However, breached was still a forum made mostly for trading illicit products and services, and what had to happen happened and pompompurin got arrested and then the other admin Baphonet decided it was better to close the forum.

The media problem
Intelx
So there is one news that was on 99% if not all articles I read. This news was that if pompompurin was arrested it was in fact cause of intelx.io, an osint and search service founded by Peter Kleissner. The history starts before breached came to life, Pompompurin had attacked intelx by indexing most of their subscription only viewable indexed files and leaking them to the public. He, with other community members also doxed Peter Kleissner and published personal information on him and his family. At the time pompompurin told that if he was doing that it was cause intelx was also indexing all of his doxbin-like paste site skidbin.net without asking permission.
Peter Kleissner also has an history of doxing in public and sharing information to law enforcement even on childrens attacking his service. This is why when pompompurin created a new account on intelx and started doing indexing the results Peter Kleissner leaked all of his account information and logs on intelx twitter and telegram and shared them with authorities. It was found that the ip used to register on intelx was a residential ip.
This is now that the problem start, when pompompurin got arrested Peter Kleissner went to twitter and told the public that it was the information he provided to the fbi that permitted pompompurin arrest. Media outlets not verifying information as always went on to write that if pompompurin has been arrested it was cause of a revolutionary osint service that helped law enforcement, intelx.
Now, what is the problem you may ask ? This ip was a residential ip so pompompurin must have forgotten to turn on his 7 proxychain right ? No. It was in fact a residential ip proxy sold by the service nsocks which mean that it was not in fact his residential ip but just an exit proxy he used.
Hydramarket
Here is another community/service pompompurin had flighted with. Hydramarket is a forum that also tried replacing raidforums but unlike breached it was founded on lies. Hydramarket funder usurped omnipotent (the now arrested raidforums funder) and lied about raidforums staff being members of his forum. He also made the forum with the only goal to make money by selling VIP subscriptions for people to access the leaked databases downloads which contains only already leaked databases. Hydramarket only power when breached was alive were ddos attacks as it is hard and costly for breached, a forum with a big infrastructure, in different countries and with not cheap hosts to handle these attacks.
When pompompurin was arrested, in intelx fashion, hydramarket went to telegram and told everyone that they were the ones that got the fbi on breached servers by sending them the backend ip of breached database server.
The problem ? Same as the one mentioned above, media outlets haven’t verified any information as if the leaked ip was really the one of breached and haven’t even verified the history of Hydramarket lying. Here is an example of a french article on the subject published by zataz.com, a media funded by Damien Bancal and known for writing dubious articles.
Direct link: https://www.zataz.com/dans-les-petits-secrets-de-la-fin-du-forum-pirate-breached/
Archive: https://archive.is/syzXS
Conclusion
To conclude, we see more and more peoples trying to educate themselves into cybersecurity for themselves but also to work on this beautiful field that is computer science. The problem however, is that if you do not know where to search and are not able to be critic towards the articles you read by fear of being in these "scarry" communities you loose most of the information and learn mostly fud.
So my advice would be to get into these communities, even if you are fully against what they do it will make you understand how they work in the real world and not only in the headlines.
Edit made on the 24/03/2022
As planed, the trial for pompompurin was today. The trial just gave us more element as how pompompurin was arrested and as expected nor intelx nor hydramarket were the cause of his arrest.
The cause of his arrest was just a bunch of stupid OPSEC mistakes:
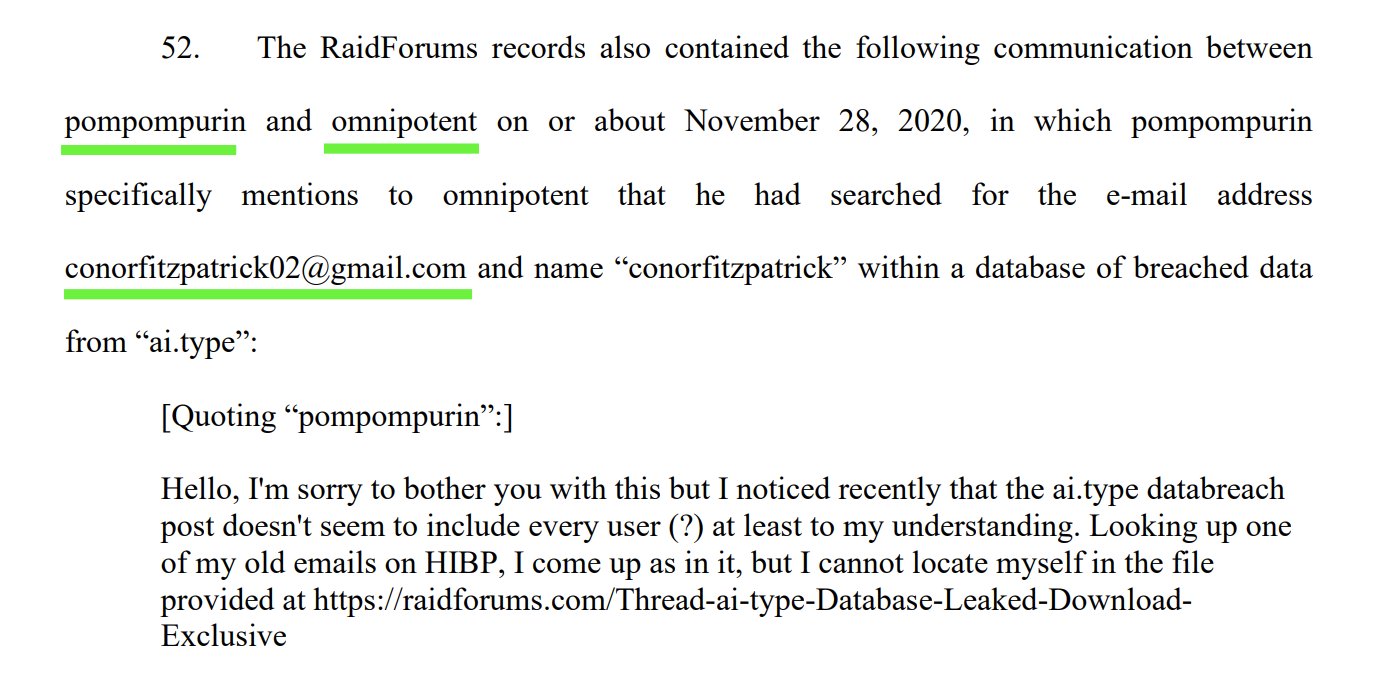
- When he messaged omnipotent, the old raidforums owner, about a leaked database which did not contain his personal email (which it should have if the database was real as he had an account). To prove his point he just sent out his personal email to omnipotent.
- When he connected to raidforums with multiple mobile ips associated with his phone.

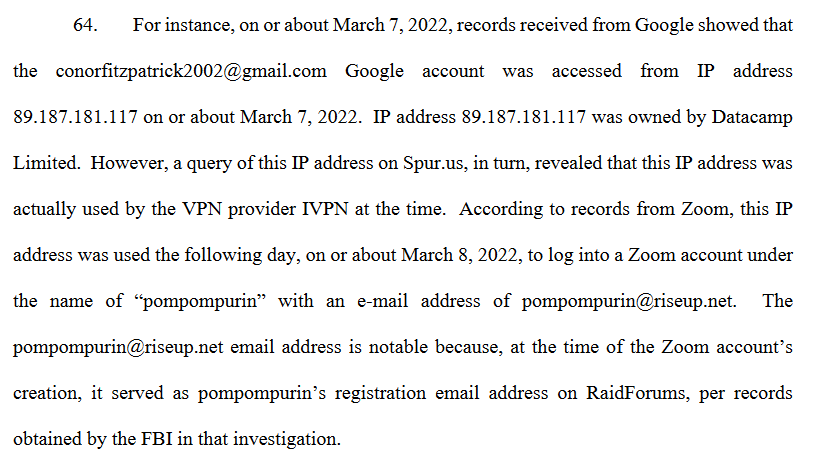
- He connected with VPNS to his personal google account at the same time as for his criminals activities.
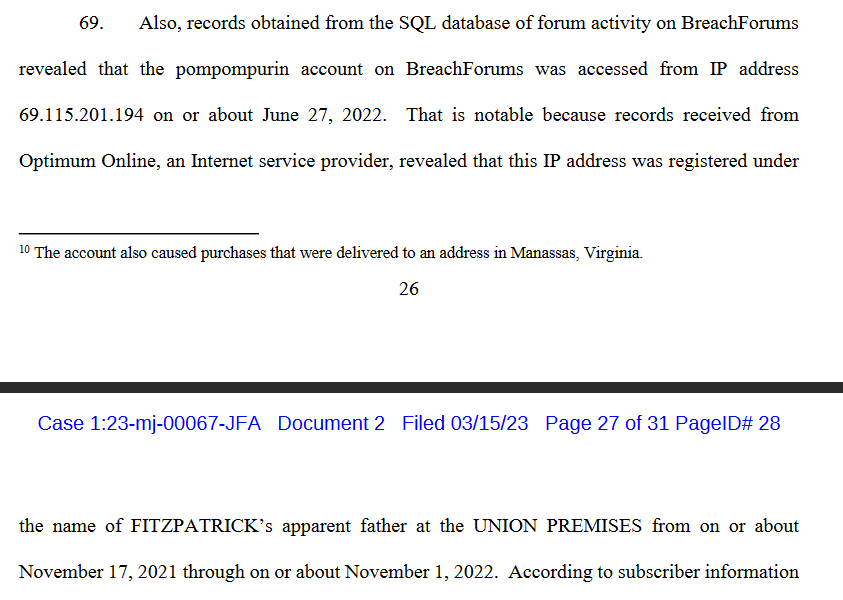
- He accessed breached on a home residential ip linked to his father name (probably his home).
And probably a lot more that I didn’t bother to include here. If you are interested to know more you should definitely read the section “Attribution of Conor Fitzpatrick as “pompompurin”” of the pompompurin affidavit.
Adding to the conclusion
What we can learn from that ? It is important to maintain a good OPSEC since the creation of your online identity and not when it is too late. You should practice your OPSEC like if your life was depending on it, because it might. You should also never trust anyone with your data and security on the internet even if they seems to be hardened OPSEC masters on the outside.